chika01 writeup
by yunaranyancat
Hello guys,
Intro
I have created my first ctf challenge called chika01 for my friends to play with. And since it has been like a week or more since I created the challenge, I think it’s time to do the writeup about it. If you have not solved it yet and wanted to give it a try, stop scrolling, download the challenge and get the secret key! ;>
Walktrough
getting the key for chikasecretmessage.zip
When we unzip the file, we will be shown with 4 files.
The zip file is currently password protected, so we need to find a way to unlock it.
The first image is chikarobotdance.png. If we do strings command or binwalk, we will find nothing there. Maybe it’s just a bait for making this challenge looks harder?
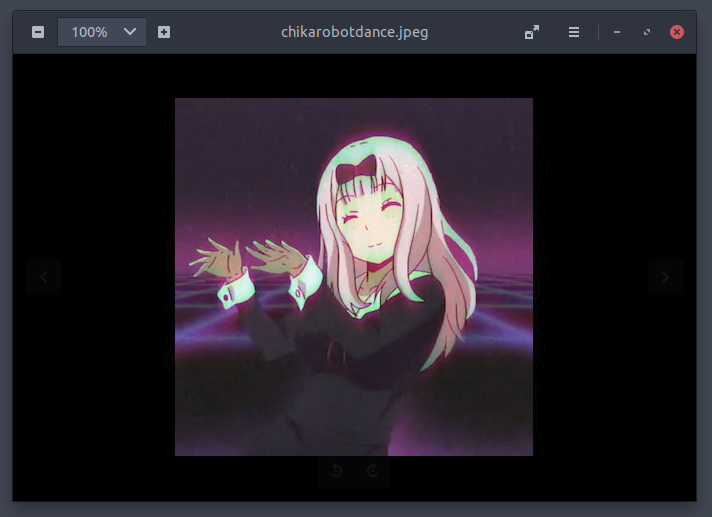
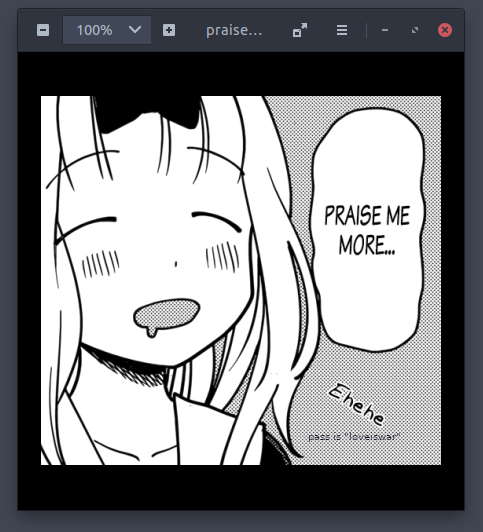
The second image is praisekawaiichikapls.png. If we look closely, at the lower right of the image, there is a text which seems like showing the password for the zip file, loveiswar.
and when we try to unzip it, the password didn’t work. So no praise for chika this time. ;{
And the last one is a text file. If we look closely, there are only 4 words that are repeated multiple times, dash , space , dot and slash .
It is actually a morse code that being translated literally from symbols to their own respective words. So, using a simple python code I wrote below, it will help us translate the words back.
f = open("random_ERROR.txt","r")
fl = f.readlines()
text = ""
for x in fl:
text += x
print(text.replace("dash","-").replace("space"," ").replace("slash","/").replace("dot","."))and we will have something like this,
- .... . / ... . -.-. .-. . - .- .-. -.-- / --- ..-. / - .... . / ... .... ..- -.-. .... .. .. -. / .- -.-. .- -.. . -- -.-- / ... - ..- -.. . -. - / -.-. --- ..- -. -.-. .. .-.. .-.-.- / ... .... . .----. ... / -... . . -. / ..-. .-. .. . -. -.. ... / .-- .. - .... / ... .... .. -. --- -- .. -.-- .- / ... .. -. -.-. . / -- .. -.. -.. .-.. . / ... -.-. .... --- --- .-.. .-.-.- / ... .... . .----. ... / -.. .. - --.. -.-- / .- -. -.. / .-.. .. -.- . ... / - --- / --. --- ... ... .. .--. --..-- / .- -. -.. / --- ..-. - . -. / - .... .-. --- .-- ... / .- / .-- .-. . -. -.-. .... / .. -. / ... .... .. -. --- -- .. -.-- .- / .- -. -.. / ... .... .. .-. --- --. .- -. . .----. ... / .--. .-.. .- -. ... / -.. ..- . / - --- / .... . .-. / ..- -. .--. .-. . -.. .. -.-. - .- -... .. .-.. .. - -.-- .-.-.- / . ...- . -. / ... --- --..-- / ... .... . .----. ... / --.- ..- .. - . / .- / -... .. - / -- --- .-. . / .-- . .-.. .-.. -....- .- -.. .--- ..- ... - . -.. / - .... .- -. / .... . .-. / ..-. . .-.. .-.. --- .-- / ... - ..- -.. . -. - / -.-. --- ..- -. -.-. .. .-.. / -- . -- -... . .-. ... / .- -. -.. / ... --- -- . - .. -- . ... / - .- -.- . ... / .. - / ..- .--. --- -. / .... . .-. ... . .-.. ..-. / - --- / - . .- -.-. .... / - .... . -- / .... --- .-- / - --- / --- ...- . .-. -.-. --- -- . / - .... . .. .-. / ... .... --- .-. - -.-. --- -- .. -. --. ... .-.-.- / - .... . / .--. .- ... ... .-- --- .-. -.. / .. ... / .-..-. .-.. --- ...- . .. ... .. -. -.. . . -.. .- .-- .- .-. .-..-. .-.-.- / - --- / .- ...- --- .. -.. / - .-. -.-- / .- -. -.. / . .-. .-. --- .-. --..-- / - .... . / .--. .- ... ... .-- --- .-. -.. / .. ... / .. -. / -.-. .- .--. .. - .- .-.. / .-.. . - - . .-. .-.-.- / - .... . / - . -..- - / -... . ..-. --- .-. . / .. ... / .--- ..- ... - / - --- / . -. -.-. --- ..- .-. .- --. . / .--. . --- .--. .-.. . / - --- / .- ..- - --- -- .- - . / - .... . / -.-. --- -. ...- . .-. ... .. --- -. / --- ..-. / - .... . / -.-. --- -.. . / .. -. ... - . .- -.. / --- ..-. / -.. --- .. -. --. / .. - / -- .- -. ..- .- .-.. .-.. -.-- .-.-.- / .. - .----. ... / . .- ... -.-- --..-- / .-. . .- .-.. .-.. -.-- .-.-.-
Using this site for example, we will get this text.
THE SECRETARY OF THE SHUCHIIN ACADEMY STUDENT COUNCIL. SHE'S BEEN FRIENDS WITH SHINOMIYA SINCE MIDDLE SCHOOL. SHE'S DITZY AND LIKES TO GOSSIP, AND OFTEN THROWS A WRENCH IN SHINOMIYA AND SHIROGANE'S PLANS DUE TO HER UNPREDICTABILITY. EVEN SO, SHE'S QUITE A BIT MORE WELL-ADJUSTED THAN HER FELLOW STUDENT COUNCIL MEMBERS AND SOMETIMES TAKES IT UPON HERSELF TO TEACH THEM HOW TO OVERCOME THEIR SHORTCOMINGS. THE PASSWORD IS "LOVEISINDEEDAWAR". TO AVOID TRY AND ERROR, THE PASSWORD IS IN CAPITAL LETTER. THE TEXT BEFORE IS JUST TO ENCOURAGE PEOPLE TO AUTOMATE THE CONVERSION OF THE CODE INSTEAD OF DOING IT MANUALLY. IT'S EASY, REALLY.
We can now unzip the file.
unzip chikasecretmessage.zip
when prompted with password, insert `LOVEISINDEEDAWAR`.extracting secret file from image
The first one is another image named chikafujiwara.jpg,

A quick binwalk command will show us that there is a file hidden inside the image. So, we can then extract it using binwalk or zip
unzip chikafujiwara.jpg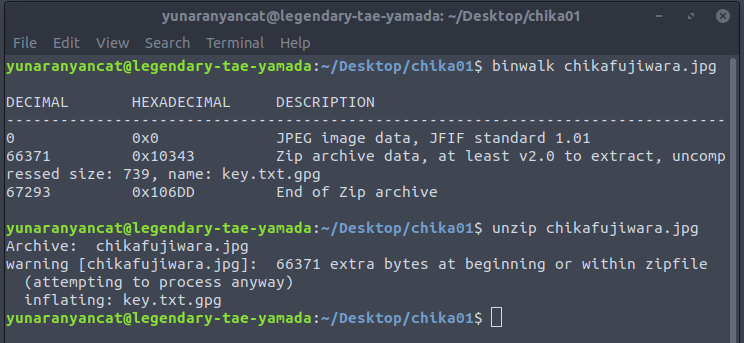
reading between the lines
and then we get a new gpg encrypted file named key.txt.gpg. So, since we didn’t have any password for the encrypted file, we can then try to get something useful from whatsapp.log.
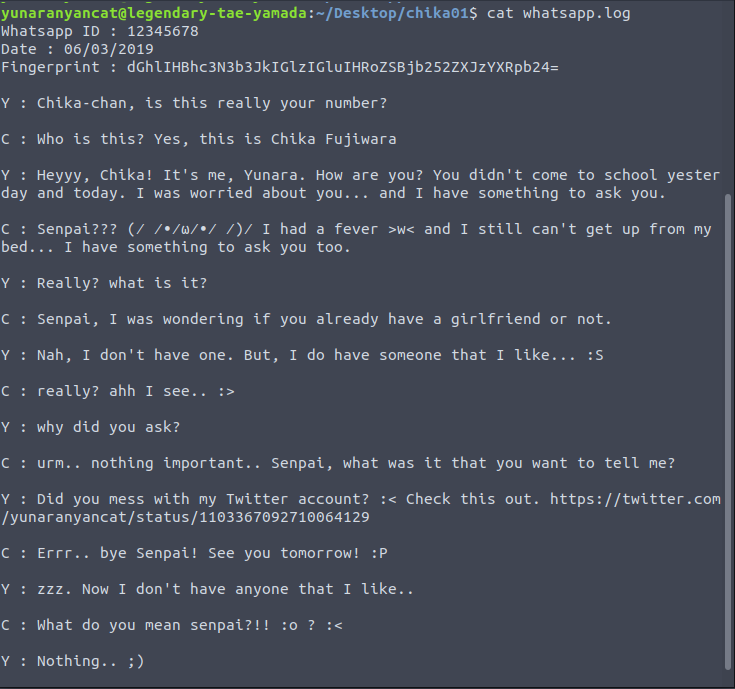
The log files showed us what it seems like a conversation of chika with another person named yunara.
At first glance of the conversation header, the fingerprint data looks like it is a base64 encoding.
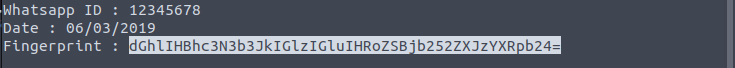
Using site like https://www.base64decode.org/ , we can see the clear text message. The decoded message is
` the password is in the conversation `.
So, it seems like we are in the right path. Let’s analyze what’s in the message.
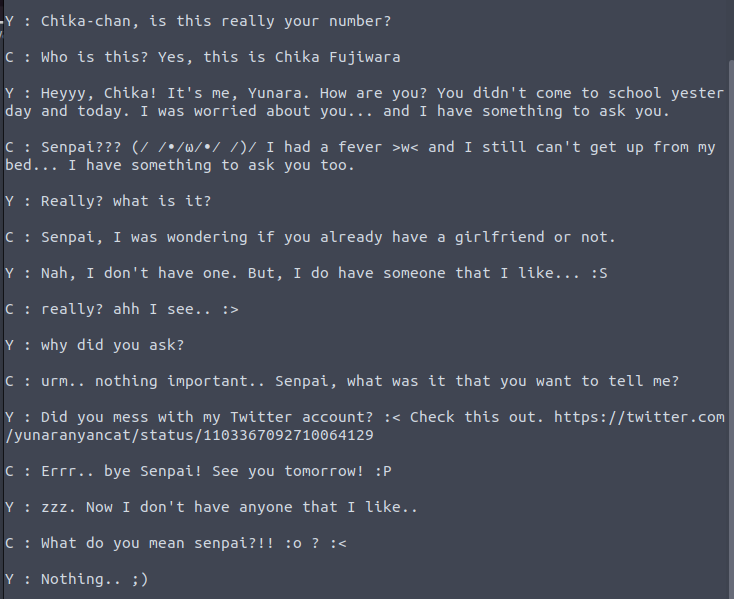
Since there is no possible password that can be guessed from the conversation, we can then try to visit the twitter link that is given,
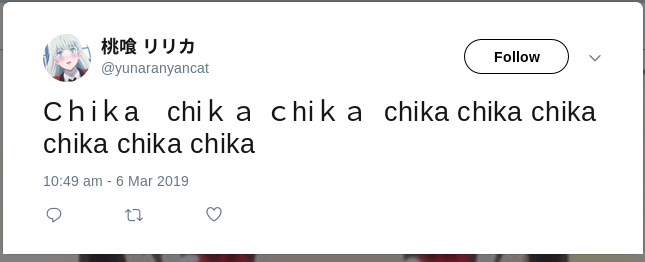
If we look closely, it seems like the tweet is using some kind of steganography. There is a github page which can hide secret messages in our tweet which is https://github.com/holloway/steg-of-the-dump. So, when we run the code,we need to paste the tweet in decode text field, then we can see that there is indeed a hidden message.
We can unlock the encrypted file using the following command.
gpg key.txt.gpg
when prompted with password, insert `mi-0w`get the right secret key
Once we open the text file, it seems like we have managed to get the secret key, which is YunaSanLoveChikaSan. Well, it’s not. :)
Actually, that is what blocking us from getting the real secret key. The symbols surrounding the fake keys are parts of an esoteric programming language which is called JSFuck . We can then remove all of the secret keys, and paste the symbols in any decoder site for example, http://codertab.com/JsUnFuck to get the clear text message.
 and voila! We finally got the secret key which is
and voila! We finally got the secret key which is yato.
Thank you
I would like to thank all of you whom have tried my challenges and for those who are interested in reading this writeup. I also would like to congratulate mucomplex for being the first person who managed to solve this mini challenge.
I’m thinking about making another challenge(s) in the future, so, for those who are interested, hit me up on Twitter so I can send a personal invitation to my next challenge(s), or if you have any idea or want to collaborate, my dm is always open.